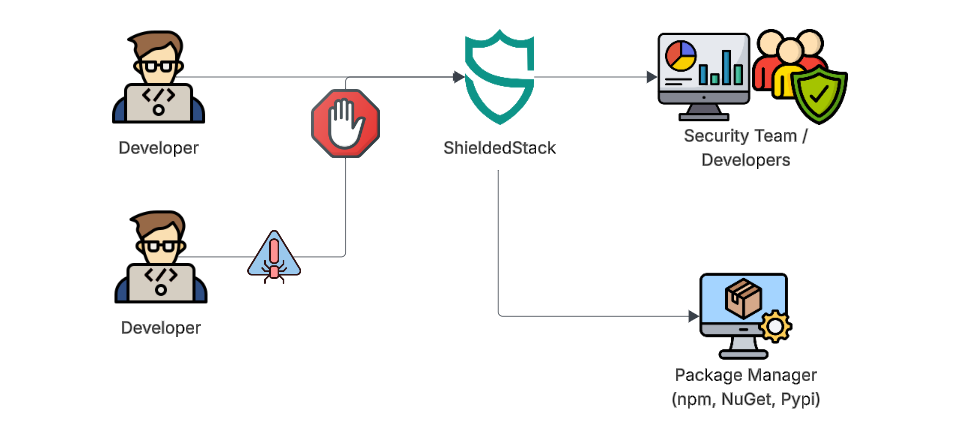
Stop Supply Chain Attacks Before They Reach Your Code
Intelligent proxy for NuGet, npm, and PyPI with real-time threat detection. Enterprise-grade security with developer-friendly setup.
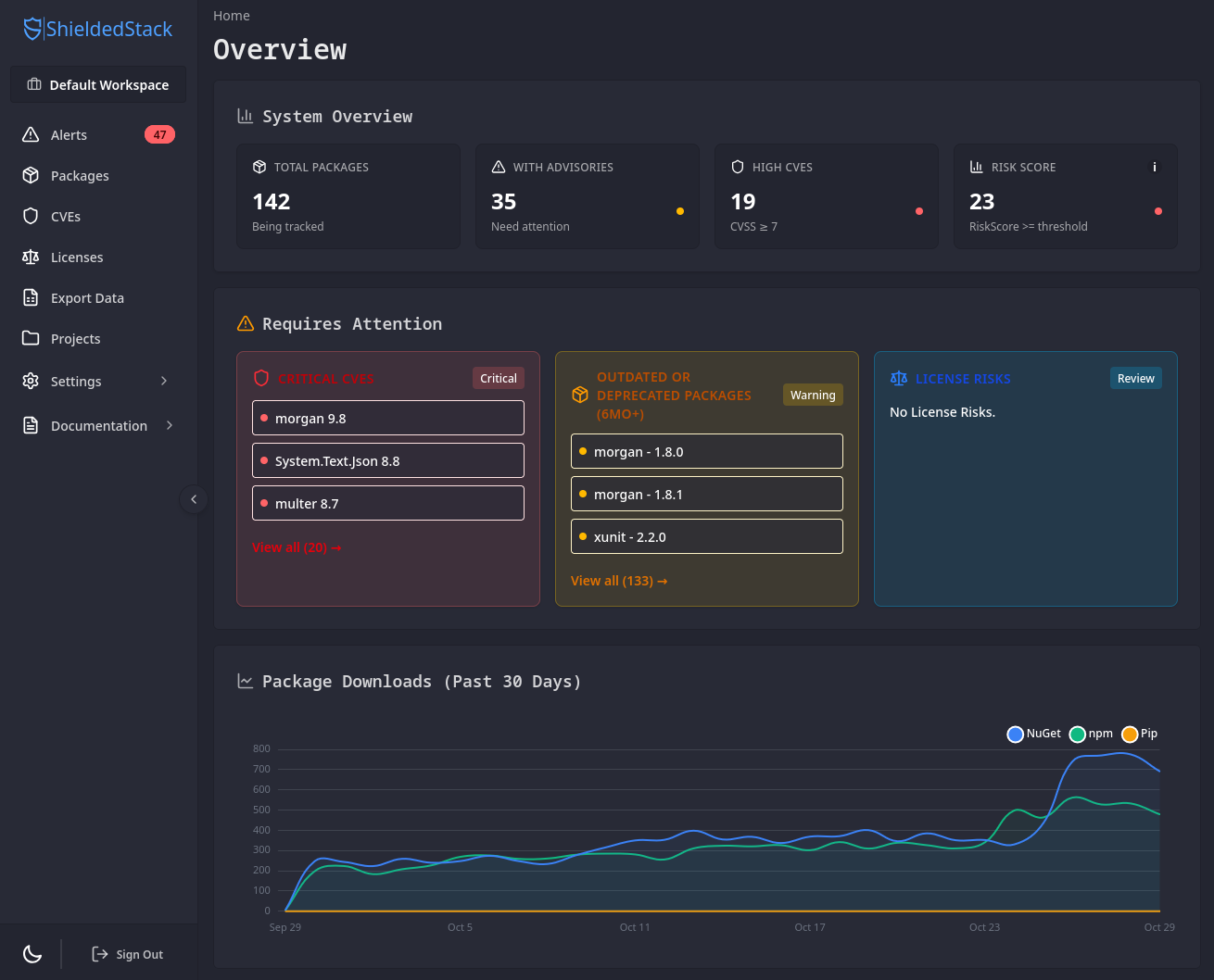
- Real-time CVE scanning & blocking
- Age-based risk & legacy detection
- Zero friction for developers
- Centralized visibility & control